
More than 60 colleges and universities competed to defend fictional energy systems from pretended hackers at DOE’s annual CyberForce Competition last month. Sandia served as a host for the first time, and organized in Albuquerque one of seven simultaneous, regional competitions across the country.
Each year, the DOE competition raises awareness of security challenges facing the nation’s critical energy infrastructure and gives students practical experience protecting simulated industrial systems, using scenarios based on real-world cybersecurity issues.
“We need to develop the next generation’s expertise so that they are combining the disciplines of cybersecurity and power engineering,” said Adrian Chavez from threat intelligence. “Because right now, these fields are mostly segregated, but they are rapidly converging in operational settings.”
That segregation exists partly because many critical systems — such as oil and water pipelines, energy grids and emergency response systems — are decades old. At the time they were built, security typically meant physically isolating them from other electronic systems. Thus, information technology and the technologies used in operating the systems evolved separately.
Today, to take advantage of new, internet-based technology, the systems need professionals who speak both languages.
CyberForce is one effort to bridge that gap.
Teams take up battle stations
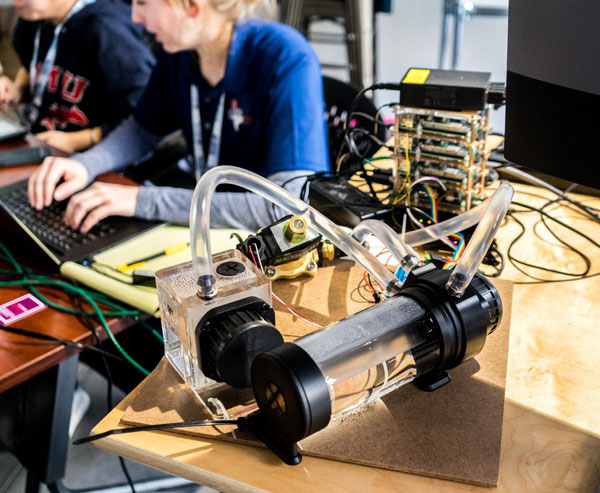
This year, each team protected an oil transport system, physically represented by a small, two-tank water pump electronically connected to a stack of Raspberry Pi computer nodes, which served as the industrial control system. A squad of volunteers, secreted elsewhere in the building and posing as regular users, could access the system through the competition’s server to perform such tasks as manually running the pump or changing the flow rate.
So could the hackers, if the students weren’t careful enough.
“Essentially, we want to try to be as stealthy as we can,” Jayson Grace said. “We, the New Mexico red team, want to try to get into the blue team’s [students’] systems and stick around—persist — so that when the competition ends, we can just ‘rm -rf /’, and you know, destroy everything.” Persistence, he explained, reflects what students should expect to see in the real world. Jayson’s group mixed brute-force attempts to guess passwords and similar clumsy attacks with other, subtler techniques.
“There are various timed vulnerabilities, such as rogue backdoors that start up on a certain port at a specific time in the competition, for which we created automated attacks,” he said. “Several red team members have been successful in breaking into their target teams’ systems, so essentially that means as soon as that service came online, we hit it and got root.”
Instant gratification, Jayson called it.
Recreating a high-consequence scenario
“We used simulated systems in the competition to learn about critical infrastructure security,” said Adrian, who built the system used in the competition. “The goal was familiarizing students to work on securing our nation’s critical infrastructure systems, which if not properly secured and exploited, could result in severe consequences.
Security for consumer electronics is rarely so dire. When a circuit breaker tripped early in the second day of the competition, computers lost power. Students were surprised and inconvenienced, but they found a quick remedy with the aid of a few extension cords, and the competition resumed.
The stakes of securing the nation’s critical infrastructure systems are much higher, said Han Lin, who managed the Albuquerque event. “Imagine you’re running an airport, directing traffic, and your whole system goes down,” he said. “How do you direct all these planes to land safely?”
Teams were mainly scored on their ability to boot hackers and minimize service interruptions. If users found a system wasn’t responding properly or they couldn’t access documentation, they punished the defenders with negative surveys, lowering their score.
Participants had a chance to earn points in the Phish Tank, where cybersecurity professionals interviewed each team and scored them on the ingenuity of their defensive strategy. There were also anomalies, distraction challenges that took participants away from their main task. When one student left his team to take care of one, he came back wearing a paper crown.
All part of the game
Government officials showed interest in the competition. Dimitri Kusnezov, the NNSA’s chief scientist and senior adviser to DOE Secretary Rick Perry, attended the Albuquerque event, as did congressional staffers on behalf of Governor-elect and New Mexico Governor-elect Michelle Lujan-Grisham, U.S. Representative Ben Ray Luján, and U.S. Senators Tom Udall and Martin Heinrich. Energy Secretary Perry delivered opening remarks by video.
The student team from Southern Methodist University of Dallas, Texas, won the Albuquerque regional competition and placed 14th overall. The national winner was the University of Central Florida.